Securing Your Group Managed Service Accounts
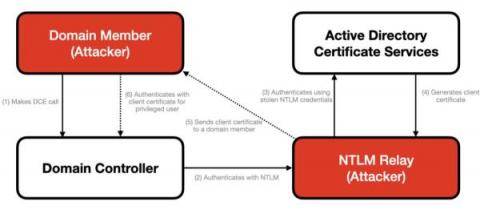
Abusing a gMSA is relatively simple conceptually. First, get its password using a tool like Mimikatz or by querying it directly due to insecure configurations in Active Directory. Since gMSAs are service accounts, they’re usually relatively privileged, so you’ll usually be able to move laterally or escalate. Let’s walk through an example scenario.