Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Audit
DataTrails: Sharing and Verifying Immutable Audit Trails
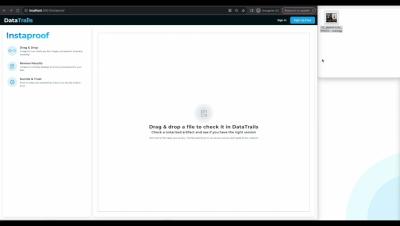
To share an immutable audit trail, you can do this with a link or a QR code that is automatically created when provenance and authenticity metadata is recorded in your DataTrails account. After you sign in to your DataTrails account on your smartphone, Anyone can use Instaproof or the DataTrails API to verify the authenticity, provenance and audit trails of public images.
Applying the Churchill Knowledge Audit to Cybersecurity
When FedEx founder Fred Smith attended Yale in the mid-1960s, he wrote an economics paper describing the concept of overnight delivery of packages by air. His professor infamously gave him a “C” grade because he viewed it as implausible. But Smith knew something his professor didn’t—and it was an idea that would change the way the business world worked forever. I bring this story up for two reasons. For one thing, I worked for FedEx and learned a lot from my time there.
Breakthrough fraud detection & content protection with watermarks + immutable audit trails
How to choose an auditor for SOC 2
TrustCloud teamed up with Dan Andrea, a partner at KLR, to discuss: Read more of Dan’s suggestions below, or check out the conversation on YouTube.
Tips for Achieving Success With a NERC CIP Audit
Electrical utilities are responsible for just about everything we do. This presents a tremendous burden on those who operate those utilities. One way these organizations offer assurance is through the audit process. While audits can generate tremendous anxiety, good planning, and tools can help make the entire process go smoothly. Moreover, these can also help to achieve positive results.
PCI 4.0: Your Next Audit May Take Longer, But it's for a Good Cause
2024 is almost here, and that means PCI DSS 4.0 will soon go into effect. The newest version will have some mandatory controls on March 31, 2024, for those who store, process, or transmit card payment data. While its predecessor weighed in at 190 pages, PCI DSS 4.0 is 486 pages and includes 63 new security controls.
What Is an Audit Trail and What Purpose Does it Serve?
Wi-Fi security auditing: Vital checks for organizational security
Cyberattacks are now more sophisticated than ever. Attackers no longer even need extensive resources and infrastructure to cause major damage. A single bad Wi-Fi connection is all it takes to overthrow all the security measures your organization has in place. In this blog, we’ll look at how you can track and monitor your Wi-Fi connections to stay off an attacker’s radar.