Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Audit
Understanding the hows and whys of open source audits
How to Perform a Cybersecurity Audit for Colleges & Universities
Cybersecurity audits are essential for any organization to review, analyze, and update its current IT infrastructure, information security policies (ISP), and overall cybersecurity risk management protocols. Audits are a critical part of information security and should be performed annually to ensure that new policies are implemented properly, potential vulnerabilities are identified, and the school maintains compliance with regulatory standards.
How Penetration Testing Can Better Prepare You for a SOC 2 Audit
The goal of a SOC 2 audit is to evaluate and verify how a service provider, whether an IT provider, Software-as-a-Service (SaaS) platform, or other outsourced solution, handles sensitive customer data. Companies are pursuing SOC 2 certification because it is an industry-recognized way to show customers that their security program is worthy of their trust. When thinking about how to prepare for a SOC 2 audit, cyber risk assessment and penetration testing should be on your list.
How to Perform a Cybersecurity Audit: A 3-Step Guide
Large-scale data breaches are flooding headlines, as major security incidents like ransomware and supply chain attacks become more strategic by the day. Organizations that fail to address their cybersecurity blindspots in such a volatile threat landscape will inevitably suffer a data breach.
The four most important aspects of software due diligence audits
Interview-based due diligence or software audits?
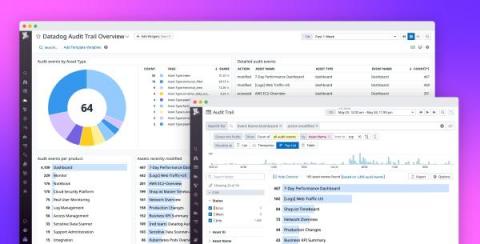
Ensure compliance, governance, and transparency across your teams with Datadog Audit Trail
In order to maintain compliance, enforce governance, and build transparency, teams across your organization need deep insight into how their users and automation interact with Datadog. For stakeholders in leadership roles, such as CIOs and CDOs, knowing what actions users took and when is essential for spotting gaps in enablement, budgeting, and reporting, as well as building a modern compliance strategy for the organization as a whole.
NERC CIP Audits: Top 8 Dos and Don'ts
My time at NERC had me involved with quite a few projects over my seven-year career there. I was involved with CIP compliance audits, investigations, auditor training, and many advisory sessions. Typically, I was advising entities across North America on different tactics, techniques, and insight from best practices I have seen. I wanted to share a few of the dos and don’ts during my experience out in the field.