Go Beyond Device Visibility to Prioritize and Act on Cybersecurity Risk
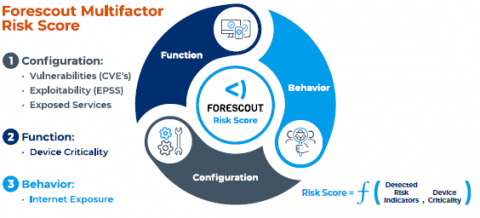
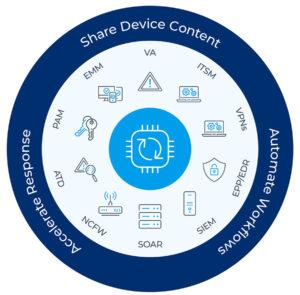
When I joined Forescout as CEO six months ago, I was excited to partner with our strong employees, management team and board as we take the company through its next phase of growth. Today I’m pleased to announce enhancements to the Forescout® Platform that will help customers fully understand the risk posture of their attack surface and enable their security teams to focus on remediating the assets that pose the most risk.