Sysdig Enriched Process Trees, an Innovative Approach to Threat Detection
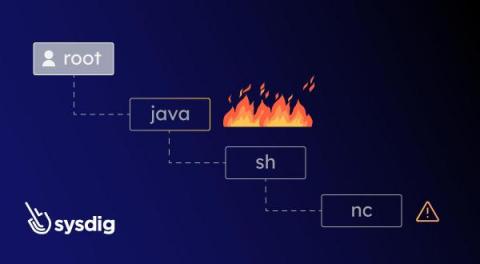
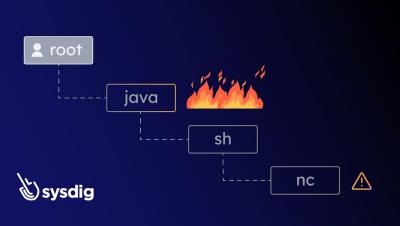
Discover how Sysdig Secure’s new Process Tree feature improves threat investigation. Imagine you’re investigating a security related detection, the investigation was triggered by the execution of stat/etc/shadow in one of your containers. Is this a sign of a legitimate activity, such as a developer debugging an app, or a sign that your container has been compromised? It depends on the context.