A peek behind the BPFDoor
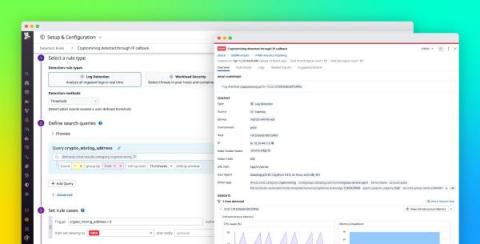
Threats knock on your door all the time. In this research piece, we explore BPFDoor — a backdoor payload specifically crafted for Linux in order to gain re-entry into a previously or actively compromised target environment. This payload has been observed across systems for five years, suggesting that the threat actors responsible for operating the malware have been around for some time and have likely operated undetected in many environments.