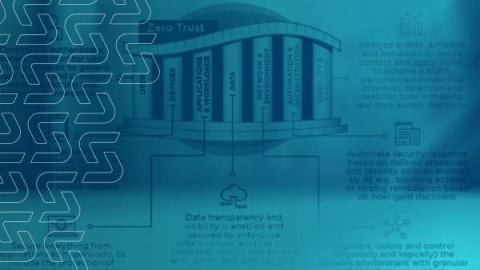
How to Apply Zero Trust Architecture (ZTA) In the Real World
How well do you sleep at night? Odds are you would sleep better if you could wake up to Zero Trust Architecture (ZTA). A true ZTA network makes incident response wake-up calls far less likely by shutting down data breaches, ransomware threats or any kind of unauthorised network access. It would also save your organisation at least £500,000 over a four-year period, making your security efforts much easier to advocate for. That’s the dream anyway.