Noname Security Platform Updates: 3.30 Release
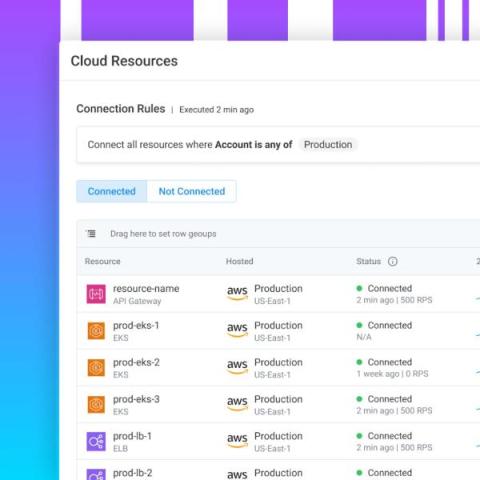
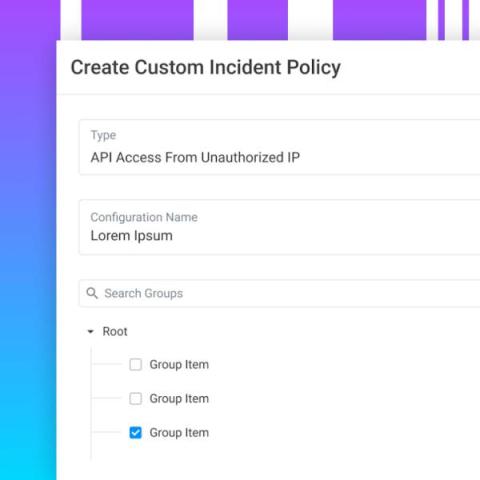
The latest Noname Security 3.30 update includes a new feature that allows for convenient tracking of attacker IP addresses, as well as improved options for triggering workflows to resolve attacks faster. Additionally, the process of installing Noname Remote Engine on local Kubernetes clusters has been simplified.