Sponsored Post
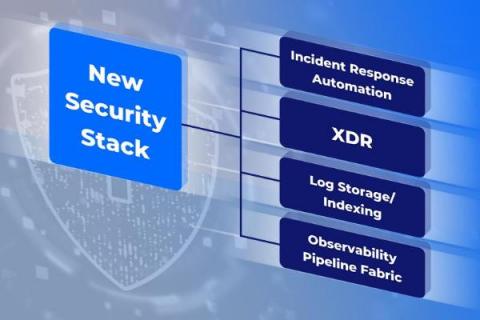
New Security Reference Stack For Modern Enterprise
The security stack is a crucial part of any company’s IT infrastructure. However, Security teams increasingly report that traditional SIEM solution approaches are “costly, complex, and resource-consuming,” according to a recent ESG survey. Fortunately, there has been significant innovation in how firms approach cybersecurity with new cloud-native technologies stack and breaking free from vendor lock-in and giving themselves more flexibility, cost advantage, and future-proofing.