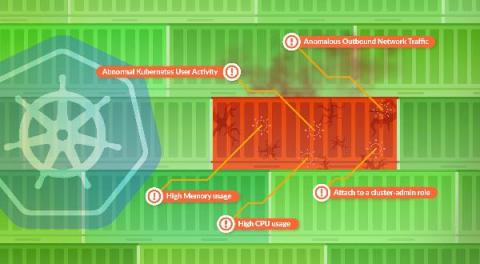
Kubernetes network segmentation using native controls
Network segmentation is almost as old as computer networking. The evolution of network segmentation went through switches to routers and firewalls, and as modern networks evolved, the ability to better control traffic by operating system native functionality evolved as well. Native controls like IP Tables became lingua franca, alongside access control lists, process isolations, and more. Native controls are not a new concept.