Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest Blogs
ISO 9000 vs ISO 9001
How to Measure and Communicate Cybersecurity Progress
Last week, SecurityScorecard was invited to participate in a fireside chat with Michael Daniel, President & CEO of the Cyber Threat Alliance (CTA). SecurityScorecard’s Chief Business Officer, Sachin Bansal, joined Daniel for a lively discussion regarding how to measure cyber health and clearly communicate progress against those metrics.
Fortifying data security: 5 features your data store must have
Unravelling the TDIR framework: Conception, evolution, and categorization
Cybersecurity is a mix of both reactive and proactive approaches. In the past, enterprises were often limited to the reactive approach. With compliance and security strategies gaining prominence, the proactive approach is also getting the spotlight. Compared to other industries, cybersecurity is highly dynamic and cybersecurity teams adopt any new technologies that can help them optimize.
A Broken Industry - 'Changing the narrative of the 'war on cybercrime'
The Future of Transactions: Understanding Secure Subscription Payment Systems
19 SEO Ranking Factors That Actually Matter in 2023
9 Common Types of Security Incidents and How to Handle Them
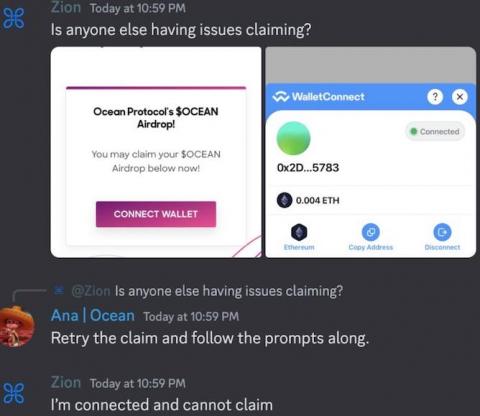
The Bookmark Trap: How Discord Admins Fell Prey to Social Engineering
Brian Krebs wrote: "A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark. "According to interviews with victims, several of the attacks began with an interview request from someone posing as a reporter for a crypto-focused news outlet online.