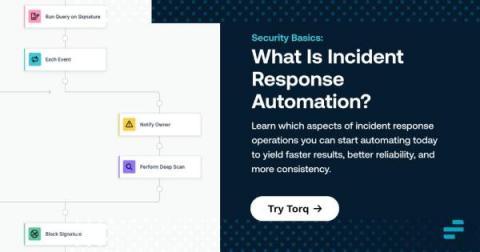
6 Steps to Successful IR: Preparation
In this blog post, we will discuss the first step in creating a successful IR plan: preparation. This step is crucial to an Incident Response Plan as this prepares your business to react when targeted by a cyber attack. This blog highlights the importance of the Preparation step and why its vital for businesses.