Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Hacking
Ethical hacker shares top tips to protect your attack surface
The underrated threat of domain takeover and hacking a firm’s internal and external attack surface can enable malicious actors to circumvent many advanced website protection mechanisms. However, Detectify Crowdsource hacker Jasmin Landry says that deploying an external attack surface management (EASM) system can help beef up your security before a malicious hacker wreaks havoc on your company. A common aphorism in cybersecurity is that there’s no such thing as perfect security.
The power grid hack on Ukraine, 2015
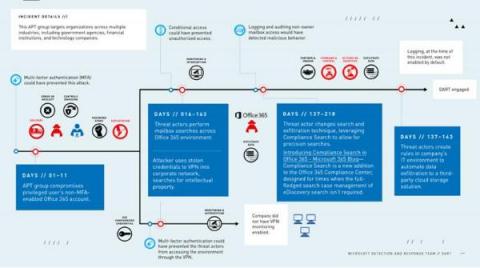
Hackers Abuse Low-Code Platforms And Turn Them Against Their Owners
Low-code development platforms open the way for greater independence and efficiency for business users. Unfortunately, they sometimes also open the way for attackers, as a result of poor low-code security practices, especially as low-code application security tries to catch up with traditional application security. Last year, Microsoft’s Detection and Response Team (DART) published the timeline of an attack which leveraged Power Platform, Microsoft's low-code platform.
How Hackers Exploit Passive and Active Attack Vectors
Learn about the methods cybercriminals use to exploit passive and active attack vectors so you can better protect your business or organization from cyberattacks. Cybercriminals will use any means they can to penetrate your corporate IT assets and exploit any vulnerabilities they find. Your ability to predict and prepare for these incidents could mean the difference between preventing a data breach and recovering from one.
Alice in Windowsland: 3 ways to escalate privileges and steal credentials
Read how our red team used different attack techniques to hack AppLocker restrictions by implementing escalated privileges and reusing the Credentials Manager to extract stored data and Azure information.
Meet a Hacker Hero - Eva Galperin
When we asked the security community who is their hacker hero, it was unsurprising to see that Eva Galperin, Director of Cybersecurity at EFF and co-founder of the Coalition Against Stalkerware was a finalist on the list. Galperin is a hacktivist known for her rage tweets that help her fight the good fight to protect vulnerable groups being targeted. Most known for her work to track down APTs, she also champions personal privacy and taking down stalkerware. Oh and she’s done a TED talk.
Opportunistic Attackers: Who Are They and How Can You Deter Them?
Meet a Hacker Hero: Hakluke
Detectify collaborates with Crowdsource, our private network of ethical hackers to help our customers access the latest critical security research and secure their web apps. With a hot hack summer, we saw a lot of devastating breaches which casted a negative view onto hackers as criminals. At Detectify, we believe that hackers are our allies.
How ethical hacker Frans Rosén deleted your Apple Shortcuts via CloudKit
SHORT SUMMARY: STOCKHOLM, SWEDEN – In February 2021, Detectify co-founder and Crowdsource hacker Frans Rosén was looking for security bugs in Apple services. Noticing that many of Apple’s own apps store their data in public databases on Apple’s data storage framework CloudKit, Frans was curious to know if any specific apps’ data could be modified with access to the public CloudKit containers in which their data was stored. Long story short, they could.