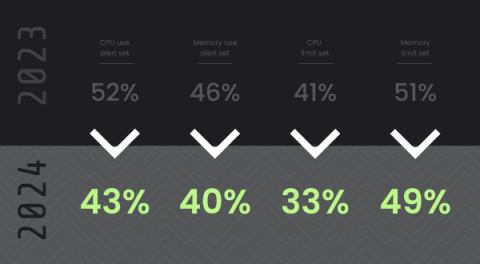
The Essential Guide to Data Monitoring
In a world where data is the new currency, understanding and leveraging data monitoring has become indispensable. Data monitoring involves systematically collecting, analyzing, and managing data to uphold its quality, security, and compliance—a critical process in a world where data influences every decision and innovation.