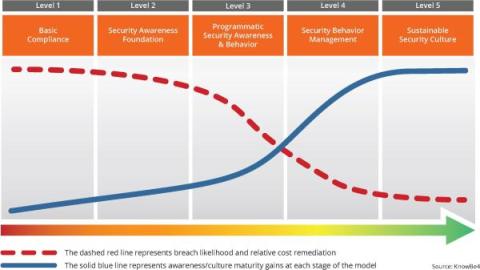
Cybercriminal Group Octo Tempest and Its Menacing Phishbait
Microsoft is tracking a cybercriminal group called “Octo Tempest” that uses threats of violence as part of its social engineering and data theft extortion campaigns. “Octo Tempest is a financially motivated collective of native English-speaking threat actors known for launching wide-ranging campaigns that prominently feature adversary-in-the-middle (AiTM) techniques, social engineering, and SIM swapping capabilities,” the researchers write.