Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2024
EP 55 - AI Insights: Shaping the Future of IAM
In this episode of Trust Issues, Daniel Schwartzer, CyberArk’s Chief Product Technologist and leader of the company’s Artificial Intelligence (AI) Center of Excellence, joins host David Puner for a conversation that explores AI’s transformative impact on identity and access management (IAM). Schwartzer discusses how CyberArk’s AI Center of Excellence is equipping the R&D team to innovate continuously and stay ahead of AI-enabled threats.
Identity Security: The Keystone of Trust
A few weeks ago, my wife asked me why stopping threat actors from impacting our lives is so difficult. In this digital age, the necessity to connect online brings inherent exposure to vulnerabilities. The challenge for you as a security leader lies in reducing the sense of vulnerability by building trust. You need to protect your organization and reassure employees so they can perform their jobs without fear.
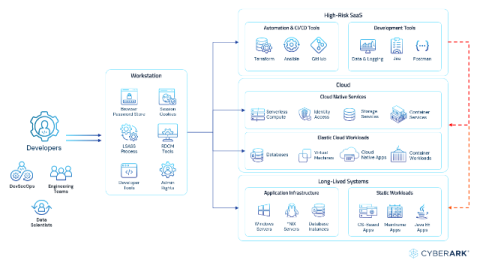
Cloud Migration Simplified: SaaS Secrets and PAM Strategy
In the era of rapid digital transformation, organizations are prioritizing cloud transformation projects to enhance their operational agility, scalability and cost efficiency. However, this shift takes time and brings significant challenges, particularly in security and identity management.
How To Configure Secure Cloud Access with ServiceNow
Welcome to our comprehensive tutorial on configuring Secure Cloud Access Integration! In this step-by-step demo, we'll show you how to streamline your access request workflows with just-in-time privilege creation and policy management. Here's what you'll learn: How end users request access through the Secure Cloud Access interface. The process of sending these requests to Cloud Workspace Owners for approval. How ServiceNow displays and manages these access requests efficiently.
"The Future of Cyberspace": CyberArk CIO Omer Grossman Keynote session at Cybertech 2024
Listen in on this insightful keynote session from Cybertech 2024, featuring CyberArk CIO Omer Grossman. In "The Future of Cyberspace," He explores the evolving landscape of cybersecurity, addressing emerging threats, innovative defense strategies and the role of advanced technologies in shaping a secure digital future. In this session, you'll learn about: Don't miss this opportunity to hear from a leading expert in the field and gain valuable knowledge that can help protect your organization in an increasingly complex cyberspace.
New Secrets Management Capabilities: CyberArk Secrets Hub, CyberArk Conjur Cloud, CyberArk Conjur Enterprise, CyberArk Credential Providers
We’re excited about several new Secrets Management capabilities that we announced at IMPACT 24 in Nashville and around the globe on the IMPACT World Tour. These include CyberArk Conjur Cloud support for Self-hosted PAM, CyberArk Secrets Hub support for Google Cloud and dramatic performance improvements for the Credential Providers with Release 14. AWS also demonstrated their new ”Managed By CyberArk“ capability in the AWS Secrets Manger UI.
Unify Identity Security with Microsoft E5 and CyberArk
In today’s dynamic threat landscape, a robust identity security strategy is paramount to protecting enterprises. With the digital perimeter extended to every user identity, securing access across your complete environment – on-premises, multi-cloud and everything in between – is no longer optional, but essential.
Financial Highwire: The Critical Role of Identity Security in Finance
In the highwire act of the financial services sector, identity security serves as the essential safety net, meticulously engineered to intercept any missteps before they precipitate a fall. Just as a tightrope walker relies on a safety net for confidence at dizzying heights, financial institutions – from global companies and insurers to community banks and credit unions – navigate a complex array of risks.
Protect Your Digital World with CyberArk and Proofpoint Browser Security!
In this video, we dive into the powerful combination of CyberArk and Proofpoint Browser Security, two leading solutions in the realm of cybersecurity. Learn how these tools can fortify your defenses against cyber threats and safeguard your sensitive information. Topics Covered: Who Should Watch: Stay Connected: Don't forget to subscribe to our channel for more insights into the latest cybersecurity trends and solutions. Hit the bell icon to get notified whenever we upload a new video!
EP 54 - Zen and the Art of CISO Leadership
In this episode of the Trust Issues podcast, we explore the nexus of mindfulness, identity security and leadership with Jitender Arora, Partner and Chief Information Security Officer (CISO) for Deloitte North and South Europe, and Deloitte’s Global Deputy CISO.
CIO POV: Building Resilience in a Complex Threat Landscape
As a CIO, I often wish for a world where the threat landscape is less expansive and complicated than it is today. Unfortunately, the reality is quite different. This month, I find myself particularly focused on the idea that our digital business would come to a grinding halt without the technology ecosystem that supports it. However, this very ecosystem also presents significant risks.
Ultimate Protection: CyberArk Secure Browser & Proofpoint Anti-Phishing Integration | CyberArk
Discover the next level of web security with the CyberArk Secure Browser! In this video, we dive into the powerful features of CyberArk's Secure Browser, designed to provide: Granular Policy Controls Data Exfiltration Prevention Session Monitoring Credential Security Privacy Enforcement But that's not all! We also explore how combining CyberArk's Secure Browser with Proofpoint's industry-leading anti-phishing capabilities offers users comprehensive, real-time protection against phishing sites attempting to steal credentials and sensitive data.
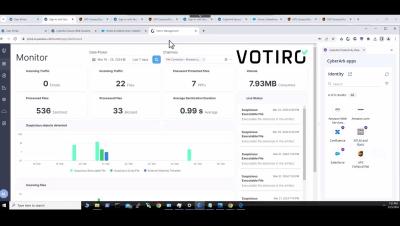
Secure Your Digital Environment with CyberArk & Votiro
Welcome to our channel! In this video, we delve into how the combined strengths of CyberArk and Votiro provide a comprehensive solution to safeguard your organization against cyber threats targeting web browsing and file content. Key Benefits: By integrating CyberArk and Votiro, your organization can enjoy a secure digital environment without compromising on user productivity or business continuity. Stay protected and efficient with our holistic cybersecurity solution.
Securing a Lifeline: Why Identity Security is Paramount in Healthcare
In the intricate healthcare ecosystem, cybersecurity is akin to the human immune system – a vital defense that safeguards the body from external and internal threats. Healthcare cybersecurity is essential for protecting patient data, ensuring medical service availability and maintaining compliance across the medical industry. The future of healthcare is increasingly digital, and its security depends on the strength of identity security measures.
Operation Grandma: A Tale of LLM Chatbot Vulnerability
Who doesn’t like a good bedtime story from Grandma? In today’s landscape, more and more organizations are turning to intelligent chatbots or large language models (LLMs) to boost service quality and client support. This shift is receiving a lot of positive attention, offering a welcome change given the common frustrations with bureaucratic delays and the lackluster performance of traditional automated chatbot systems.
Triage Your Cloud Security: Risk Prioritization Methods
It’s a familiar post-disaster scene in seemingly every television medical drama. A ferry has crashed, or a train has derailed. Patients flood into the ER, each requiring urgent medical attention. The impossibly attractive medical staff must quickly assess and prioritize patients based on the severity of their injuries and the likelihood of survival. Someone with great hair likely says an inspiring quote and jumps immediately into action.
UiPath CyberArk CCP Integration Conjur Cloud
Welcome to our latest video where we dive into the world of Conjur Cloud! Conjur Cloud is a cutting-edge SaaS-based, cloud-agnostic solution designed specifically for secrets management. It offers organizations a robust platform to secure non-human access to secrets, eliminating the notorious "secret zero" problem once and for all.