Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Application Security
The latest News and Information on Application Security including monitoring, testing, and open source.
Winning Management Support as an AppSec Leader
As an Application Security (AppSec) leader, one of the most significant challenges you might face is securing management support for your program. This lack of support often results in under-resourced AppSec teams feeling frustrated and unable to make a meaningful impact. To foster an environment where your team feels valued and prevents burnout, AppSec leaders must prioritize gaining additional resources. In many organizations, security tends to climb the priority ladder slowly, requiring AppSec leaders to put in extra effort to secure the necessary approvals. Here are three strategies that can help you win management buy-in and create a better environment for your team.
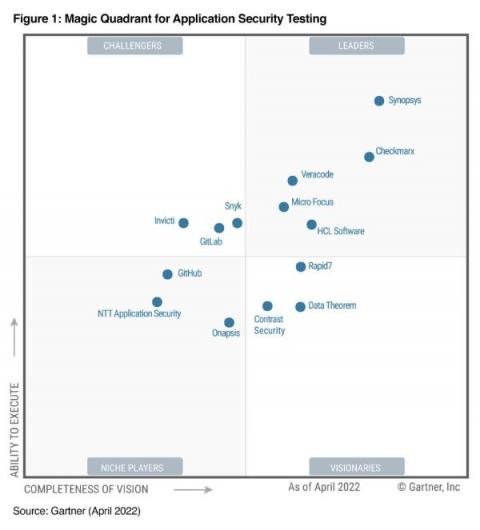
Synopsys named a Leader in the 2023 Gartner Magic Quadrant for Application Security Testing for the seventh year
In the 2023 Gartner® Magic QuadrantTM for Application Security Testing, Synopsys placed highest and furthest right for the fifth consecutive year for our Ability to Execute and our Completeness of Vision.
Magic Quadrant for Application Security Testing, 2023 Gartner report
We’re proud to announce that Mend.io has been recognized as a Visionary in the 2023 Gartner Magic Quadrant for Application Security Testing (authors Mark Horvath, Dale Gardner, Manjunath Bhat, Angela Zhao, Ravisha Chugh); (May 17, 2023).
A New Era of AppSec: 10 Times as a Leader in Gartner Magic Quadrant for Application Security Testing
Ten represents the completion of a cycle and the beginning of a new one, as there are ten digits in our base-10 number system. We've scanned nearly 140 trillion lines of code, so we can’t help but pick up on the one and the zero in our exciting announcement. It's the tenth publication of the Gartner® Magic Quadrant™ for Application Security Testing (AST), and we are pleased to announce we are a Leader for the tenth consecutive time.
Leveraging Security Asset Inventories
Cloud Security: Turns Out We Needed Another Acronym (CNAPP)
Gartner’s 2023 “Market Guide for Cloud-Native Application Protection Platforms” (CNAPP) caused some security leaders to question whether they need yet another tool to protect the complex beast that is the cloud. Procuring yet another shiny security product is probably not how you earn the envy of your peers, but if your organization relies on shipping secure applications fast, then CNAPP should be on your radar. What exactly is CNAPP?
Security success in the Bay Area
Application security is constantly evolving — and there’s no better place to observe these changes than in the Bay Area. Silicon Valley is home to thousands of companies attempting to solve a multitude of problems, but one thing they all have in common is the often daunting task of risk mitigation.