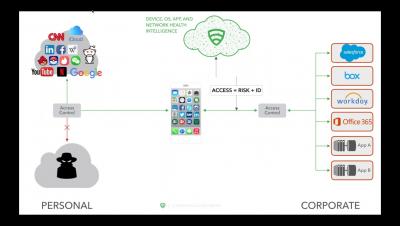
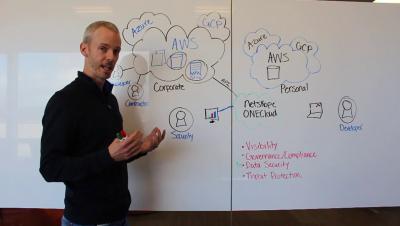
Internet of Termites
Termite is a tool used to connect together chains of machines on a network. You can run Termite on a surprising number of platforms including mobile devices, routers, servers and desktops. That means it can be used used to bounce a connection between multiple machines, to maintain a connection that otherwise wouldn’t be possible.