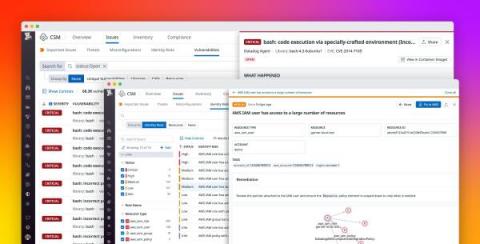
Mitigate identity risks and infrastructure vulnerabilities with Datadog Cloud Security Management
Cloud environments comprise hundreds of thousands of individual components, from infrastructure-level containers and hosts to access-level user and cloud accounts. With this level of complexity, it’s important to establish and maintain end-to-end visibility into your environment for many reasons—not least among them to efficiently identify, prioritize, and mitigate security threats.