Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CyberArk
EP 55 - AI Insights: Shaping the Future of IAM
In this episode of Trust Issues, Daniel Schwartzer, CyberArk’s Chief Product Technologist and leader of the company’s Artificial Intelligence (AI) Center of Excellence, joins host David Puner for a conversation that explores AI’s transformative impact on identity and access management (IAM). Schwartzer discusses how CyberArk’s AI Center of Excellence is equipping the R&D team to innovate continuously and stay ahead of AI-enabled threats.
Identity Security: The Keystone of Trust
A few weeks ago, my wife asked me why stopping threat actors from impacting our lives is so difficult. In this digital age, the necessity to connect online brings inherent exposure to vulnerabilities. The challenge for you as a security leader lies in reducing the sense of vulnerability by building trust. You need to protect your organization and reassure employees so they can perform their jobs without fear.
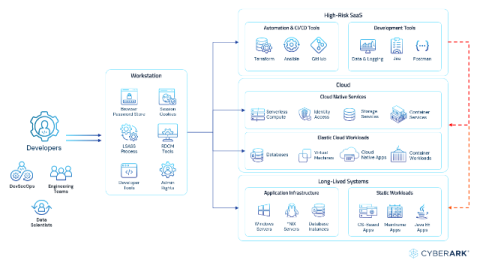
Cloud Migration Simplified: SaaS Secrets and PAM Strategy
In the era of rapid digital transformation, organizations are prioritizing cloud transformation projects to enhance their operational agility, scalability and cost efficiency. However, this shift takes time and brings significant challenges, particularly in security and identity management.
How To Configure Secure Cloud Access with ServiceNow
Welcome to our comprehensive tutorial on configuring Secure Cloud Access Integration! In this step-by-step demo, we'll show you how to streamline your access request workflows with just-in-time privilege creation and policy management. Here's what you'll learn: How end users request access through the Secure Cloud Access interface. The process of sending these requests to Cloud Workspace Owners for approval. How ServiceNow displays and manages these access requests efficiently.
"The Future of Cyberspace": CyberArk CIO Omer Grossman Keynote session at Cybertech 2024
Listen in on this insightful keynote session from Cybertech 2024, featuring CyberArk CIO Omer Grossman. In "The Future of Cyberspace," He explores the evolving landscape of cybersecurity, addressing emerging threats, innovative defense strategies and the role of advanced technologies in shaping a secure digital future. In this session, you'll learn about: Don't miss this opportunity to hear from a leading expert in the field and gain valuable knowledge that can help protect your organization in an increasingly complex cyberspace.
New Secrets Management Capabilities: CyberArk Secrets Hub, CyberArk Conjur Cloud, CyberArk Conjur Enterprise, CyberArk Credential Providers
We’re excited about several new Secrets Management capabilities that we announced at IMPACT 24 in Nashville and around the globe on the IMPACT World Tour. These include CyberArk Conjur Cloud support for Self-hosted PAM, CyberArk Secrets Hub support for Google Cloud and dramatic performance improvements for the Credential Providers with Release 14. AWS also demonstrated their new ”Managed By CyberArk“ capability in the AWS Secrets Manger UI.
Unify Identity Security with Microsoft E5 and CyberArk
In today’s dynamic threat landscape, a robust identity security strategy is paramount to protecting enterprises. With the digital perimeter extended to every user identity, securing access across your complete environment – on-premises, multi-cloud and everything in between – is no longer optional, but essential.
Financial Highwire: The Critical Role of Identity Security in Finance
In the highwire act of the financial services sector, identity security serves as the essential safety net, meticulously engineered to intercept any missteps before they precipitate a fall. Just as a tightrope walker relies on a safety net for confidence at dizzying heights, financial institutions – from global companies and insurers to community banks and credit unions – navigate a complex array of risks.