Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Rubrik
Make Account Compromise a Non-Issue: Introducing Immutability for Microsoft Azure VMs
Author Brian Mislavsky Rubrik Storage Tiering for Microsoft Azure now leverages Azure Blob immutability by default. In our Winter Release, we introduced Storage Tiering for Microsoft Azure as a way for Rubrik customers to further protect workloads in Microsoft Azure by enabling the ability to logically air gap data between Azure Subscriptions as well as potentially decrease long term storage costs by almost 40%.
Worried about ransomware? Start with a plan
You don’t need me to tell you what a ransomware attack could do to your business. We’ve all read the stories. Even the largest multinationals have been crippled by malware encrypting or stealing sensitive data. The result is a Hobson’s choice for IT managers: pay the criminal gang an exorbitant ransom demand or face costly downtime, reputational damage, and regulatory scrutiny. Thankfully, your fate is in your hands. Ransomware attacks aren’t random.
Take a Look Into the Rubrik Platform
What Does Defense-in-depth Mean and How Does it Bring Infrastructure and Data Security Together?
With the rise of ransomware and cyber attacks, the term defense-in-depth has risen to the forefront, but what exactly does it mean? At its core, defense-in-depth is a protection mechanism for network security–an approach that involves layering or using multiple controls in series to protect against possible threats. This layered concept provides multiple redundancies in the event systems and data are compromised.
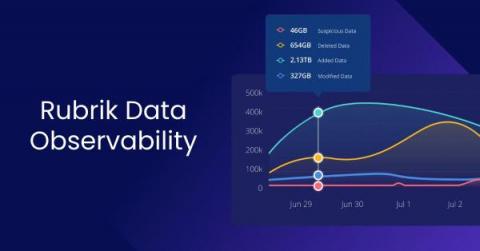
Monitoring Data Risks & Investigating Threats Faster With the Rubrik Data Observability Engine
Why is it that the most impressive technologies are often the ones that go unnoticed? Sometimes what makes technology impressive is precisely that it goes unnoticed, and that is the case with the Rubrik Data Observability engine. As ransomware continues to grow as a real, costly, and persistent threat to conducting business, organizations are looking for smarter and faster ways to keep data safe and recover easily in the face of cyber attacks.
Become Unstoppable with the Rubrik Data Security Command Center
From technology to healthcare to governments, ransomware is disrupting business like never before. Security teams are reevaluating their overall security posture and taking additional measures to secure their data. During this process, they are discovering that they don’t know if their organization’s data is fully secure and whether it will be available when they need it.
Stronger Cybersecurity, Thanks to the New Rubrik Security Cloud
Sad fact: cyberattacks continue to grow in volume and sophistication. Plus, ransomware doesn't hit like a bomb–it’s often more like a Trojan Horse, where many organizations don't realize they are under attack until it's too late. Despite investments in infrastructure security tools deployed at the endpoint, perimeter, and network, bad actors are still getting through to hold data for ransom.
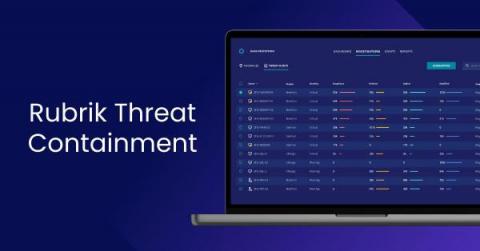
Threat Containment: Contain the Threats, Recover the Data
A common mistake made in responding to ransomware is rushing through a recovery only to realize that the recovery point was a compromised copy of the system, and in turn, re-introduces the threat back into the environment. To make matters worse, if a replicated copy were to be recovered at a tertiary site, it might introduce malware into networks that it previously didn’t have access to and further impact business operations.
Why Hackers Are Targeting Microsoft 365
It’s no secret that hackers are attracted to large and lucrative targets in the vast digital sphere. Oftentimes, the largest targets present the most avenues for attack. And with over 300 million users worldwide, Microsoft 365 is one of those large targets. Over 80% of deployed Microsoft 365 accounts have suffered an email breach and over 70% have suffered an account takeover.