Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Splunk
Connecting the dots for security analysts
Upping the Auditing Game for Correlation Searches Within Enterprise Security - Part 1: The Basics
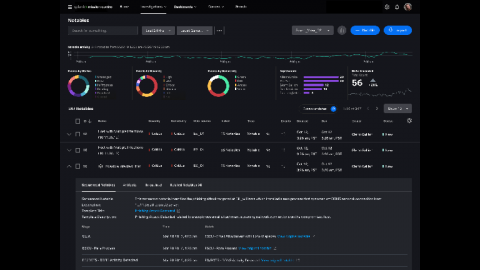
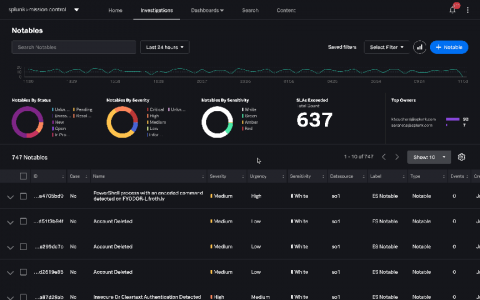
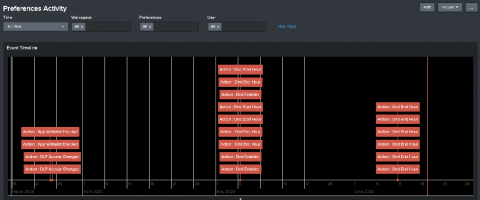
One question I get asked frequently is “how can I get deeper insight and audit correlation searches running inside my environment?” The first step in understanding our correlation searches, is creating a baseline of what is expected and identify what is currently enabled and running today. Content Management inside Splunk Enterprise Security is a quick way to filter on what is enabled (and it’s built into the UI and works out of the box).
A Day in the Life: Secrets of a Top Splunk Security Analyst
At Splunk, we’re proud to employ some of the top security analysts in the industry. On any given day, they’re investigating security incidents, triaging alerts and identifying threats so our systems and data — as well as those of our customers — remain secure. But what, exactly, do Splunk security analysts do? And what are some of their biggest challenges?
Using Splunk to Detect Abuse of AWS Permanent and Temporary Credentials
Amazon Web Services provides its users with the ability to create temporary credentials via the use of AWS Security Token Service (AWS STS). These temporary credentials work pretty much in the same manner like permanent credentials created from AWS IAM Service. There are however two differences.
A Unified Security Operations Platform: Splunk Mission Control
Security is easy, right? Get yourself a patchwork of security point products meant to solve one or two specific problems, and your organization is safe from threats! Ah, if only it were that simple… In reality, security operations are disjointed and complex. Security visibility and functionality (i.e. threat detection, investigation, containment and response capabilities) are often divided among a multitude of different security products (e.g.
The New Normal: Organizations Need Security Leaders More Than Ever
The world is changing at a pace not seen in modern history. Security leaders, including chief information security officers (CISOs), face new security challenges as well as opportunities. As COVID-19 drives workers to look for new ways to live and work, organizations must be proactive. The ‘new normal’ may seem scary at first, but savvy CISOs who see beyond tactical changes to the threat landscape can capitalize on opportunities.
Splunking Slack Audit Data
The Slack Audit Logs API is for monitoring the audit events happening in a Slack Enterprise Grid organization to ensure continued compliance, to safeguard against any inappropriate system access, and to allow the user to audit suspicious behavior within the enterprise. This essentially means it is an API to know who did what and when in the Slack Enterprise Grid account. We are excited to announce the Slack Add-on for Splunk, that targets this API as a brand new data source for Splunk.
CI/CD Detection Engineering: Splunk's Security Content, Part 1
It's been a while since I've had the opportunity to take a break, come up for air, and write a blog for some of the amazing work the Splunk Threat Research team has done. We have kept busy by shipping new detections under security-content (via Splunk ES Content Update and our API). Also, we have improved the Attack Range project to allow us to test detections described as test unit files.
Nation-State Espionage Targeting COVID-19 Vaccine Development Firms - The Actions Security Teams Need To Take Now!
Throughout the duration of COVID-19, there have been consistent rumors of increased nation-state espionage. In parallel, many recent ransomware strains have a COVID-19 tie-in. Now the United Kingdom's National Cyber Security Centre (NCSC), published an advisory report that the threat group APT29 is targeting governmental, diplomatic, think-tank, healthcare and energy targets for intelligence gain which are involved in COVID-19 vaccines development and testing.