Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Splunk
Protecting Your Assets: It's Not Just About Servers and Laptops!
In most of our blogs, we spend a TON of time going on about protecting our endpoints, looking at sysmon, checking the firewall, correlating IDS data and the like… Today, we're going to shift gears a bit and look at security from a different angle. Recently, there has been a tremendous focus on the shifting paradigm of a workforce that primarily resides in corporate offices, to a highly virtual workforce sitting at their kitchen tables.
Ransomware: How to Combat a Growing Threat to Your Organization
Ransomware is a serious threat to institutions of all kinds, resulting in mounting costs for organizations that must literally pay ransom to regain access to their essential systems. A ransomware attack takes place when a cybercriminal denies an organization access to the data it needs to conduct business, usually by encrypting the data with a secret key. The attacker then offers to reveal the encryption key in exchange for a payment. The payment can vary in amount or kind.
Between Two Alerts: Phishing Emails - Don't Get Reeled In!
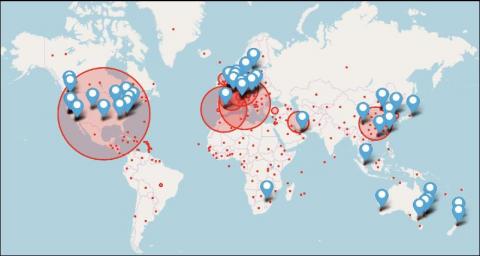
Potential attackers are really good at what they do. Security analysts see this firsthand with the amount of phishing emails their organizations see daily. A newly released State of the Phish report reveals that nearly 90% of organizations dealt with business email compromise (BEC) attacks in 2019. End users reported 9.2 million suspicious phishing emails globally for the year.
Zoom in on Security in a Remote Work World
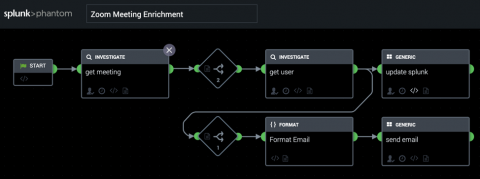
Our world has been turned upside down by COVID-19. Whether it's strategically planning our grocery run decontamination process, or trying to keep the kids quiet for even one single moment while on a conference call — things are different. One very evident difference is the change in the way we meet with each other. And one technology enabling this change is Zoom.
Hunting COVID Themed Attacks With IOCs
This blog post is part twenty-four of the "Hunting with Splunk: The Basics" series. I've been dealing with viruses for years, but this is the first time I've written a blog post where we are dealing with actual viruses. Ever since the 2004 tsunami, I have witnessed cyber-baddies using current events to trick users into opening documents or clicking on links. The COVID-19 breakout is no different.
Fraud Detection: WFH Leading to Increased BEC and Phishing Threats - What To Look For
A lot has changed in the past few weeks. And the percentage of us working from home (WFH) has increased tremendously. With increased WFH, we rely more on email communication, and this increases the opportunities for abuse by others. One thing that has stayed constant: bad people want to do bad things. As we have seen in the past, when one avenue of attack is restricted, the fraudsters redouble their efforts in other areas, and online fraud attempts are already increasing during our new normal.
Top 10 Things Keeping CISOs Up at Night in 2020
Chief information security officers (CISOs) face no shortage of challenges. Expanding attack surfaces and complex cloud security environments have given rise to new advanced threats. Compliance regulations have become more rigorous and punitive. And while digital transformation accelerates the pace of doing business, its impact is often limited by budget restrictions and security talent gaps. At Splunk we talk to hundreds of CISOs every year. Here's what they told us they care about in 2020.
Recapping the Splunk for CMMC Solution Launch
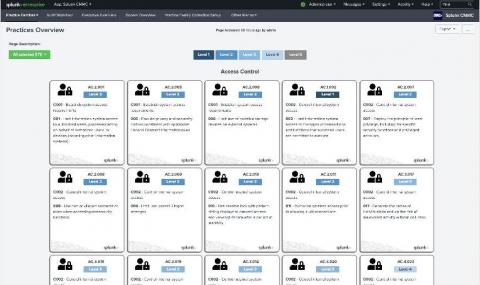
On Wednesday, March 25th, we launched our Splunk for CMMC Solution with a webinar presentation to a diverse set of defense industrial base (DIB) participants and partners. As I discussed during the launch event, the Splunk for CMMC Solution provides significant out-of-the-box capabilities to accelerate organizations’ journeys to meet, monitor, track, and mature the cybersecurity practices required by the Cybersecurity Maturity Model Certification (CMMC).
Between Two Alerts: Easy VPN Security Monitoring with Splunk Enterprise Security
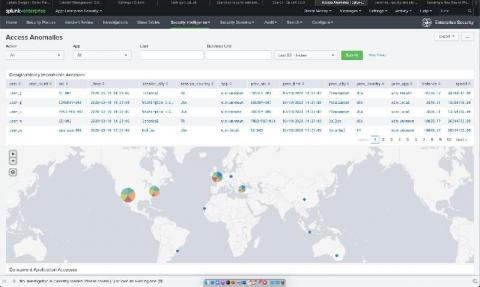
Welcome to the new world, my friends. Now that working from home is our new reality, we've found that many of our customers are taking a much closer look at the technology that binds us all together and allows us to access corporate resources: the humble VPN. In the spirit of enablement, I’ve put together a quick list of dashboards that can help add that extra bit of visibility for our faithful Splunk Enterprise Security customers.