Why Reduce Software Supply Chain Risks with Intelligent Software Security
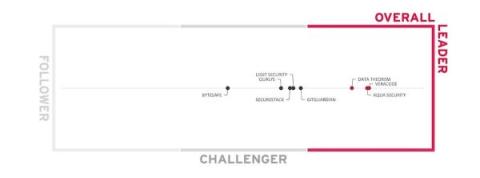
There’s a growing array of risks lurking within the supply chain of the digital solutions we increasingly depend upon. Leaving gaps in your software supply chain security (SSCS) could spell disaster for your organization. Let’s explore how new analysis defines an end-to-end solution and why Veracode was ranked as an Overall Leader, Product Leader, Innovation Leader, and Market Leader in the Software Supply Chain Security Leadership Compass 2023 by KuppingerCole Analysts AG.