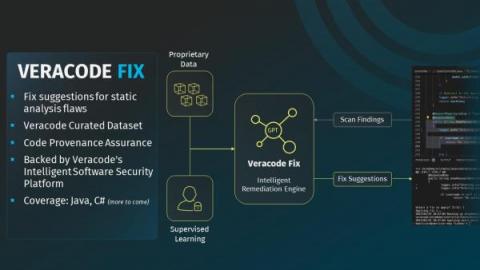
How to Measurably Reduce Software Security Risk with Veracode Fix
Veracode Fix is now available as an add-on to Veracode Static Analysis for customers on the North American instance. Availability for customers on Veracode’s EMEA and FedRAMP instances will be coming soon!