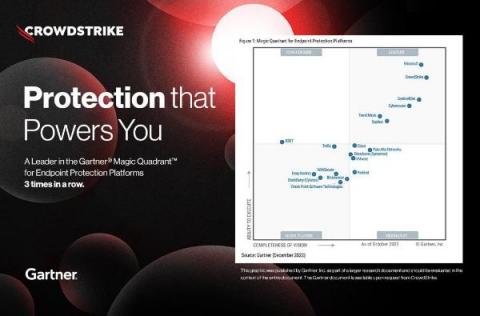
CrowdStrike Falcon OverWatch Insights: 8 LOLBins Every Threat Hunter Should Know
After dissecting a full year’s worth of interactive intrusion data, the CrowdStrike® Falcon OverWatch™ Elite team has identified the most commonly abused living-off-the-land binaries — and distilled the critical insights that defenders need to know to protect their organizations against the misuse of these binaries.