Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Intelligence
Trustwave Threat Intelligence Briefing: The 2023 Retail Services Sector Threat Landscape
The holiday shopping season is teed up for its annual explosion of spending. Retailers know this, consumers know this, cybercriminals know this, and are unfortunately ready to take advantage of any weak link that can be found to steal vital consumer and business data. However, unlike gift buyers heading to stores or shopping online on Black Friday and Cyber Monday, these adversaries are not seasonal actors.
A recipe for burnout? Survey shows over 90% of cybersecurity professionals work while on vacation
Now that the calendar has flipped to November, the end of the year is in sight. It’s a popular time for friends and family to gather for the holidays, yet unfortunately, it’s also a popular time for cyber attackers to ramp up their exploits. Our thoughts turned to the cyber professionals on the front lines. What compromises do they feel pressured to make in their work-life balance to keep their companies secure? How often does their work actually impinge on their personal time?
Enhancing Cybersecurity in the Entertainment and Gaming Industries
The Entertainment and Gaming industries are thriving economies that cater to the enjoyment needs of millions worldwide. However, these sectors are far from immune to the growing threat of cyberattacks. In fact, they’re increasingly becoming a prime target for malicious cyber threat actors due to its widespread visibility and the perception that gamers and media consumers may be less vigilant about cybersecurity.
Applying an intelligence-based approach to Cybersecurity; SIEM and dark web monitoring
“History repeatedly has demonstrated that inferior forces can win when leaders are armed with accurate intelligence.” – Central Intelligence Agency; Intelligence in War In the ever-changing landscape of global cybersecurity, the boundaries between traditional military intelligence and cybersecurity are increasingly blurred. At the heart of this convergence lies the science of intelligence analysis—a process fundamental to both realms.
The Ultimate Guide to Cyber Threat Intelligence
In an era where cyber threats are increasingly sophisticated and ubiquitous, businesses must remain vigilant and proactive in their approach to security. Cyber threat intelligence (TI or CTI) emerges as a beacon of hope, offering insights and strategies to detect, prevent, and respond to potential cyberattacks. Through this guide, we'll walk you through what TI is, different types of TI, and how it reshapes our understanding of cybersecurity.
Empowering a Secure Digital Future with Centripetal Ireland During Cybersecurity Awareness Month
In today’s digital world, the importance of cybersecurity is more critical than ever. With the constant evolution of cyber threats, safeguarding sensitive data and digital assets has transitioned from an option – to an absolute necessity. Each October, Cybersecurity Awareness Month focuses on the importance of cybersecurity in our interconnected world.
Birds of a Feather: Collaboration and Sharing within the Exclusive ThreatQ Community
Over the past decade, ThreatQuotient has dedicated itself to the task of transforming obscure digital threat data into actionable intelligence. Throughout this period, we’ve earned the trust of our partners and customers, forging strong relationships with each of them. Each team we’ve encountered in the field has brought unique insights, skill sets, perspectives, and ideas, significantly influencing our approach and perception of the ever-evolving threat landscape.
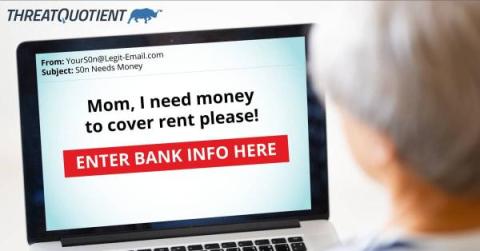
Don't Take the Bait: Recognize and Report Phishing Attempts
Phishing attacks, which involve fraudulent attempts to trick individuals into divulging sensitive personal information, remain a significant threat. Despite advances in cybersecurity, hackers continue to adapt and evolve their tactics to exploit vulnerabilities.
Keep Your Software Update Routine Strong
Software is an essential part of our online experience. Whether it’s our operating systems, web browsers, or the apps we use daily, software plays a crucial role in our lives. However, with great convenience comes a big responsibility, and one of the most essential aspects of online safety is keeping your software updated regularly. In this blog, we’ll explore the significance of keeping your software up-to-date.