Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Snyk
Chatting with the Log4JShell Bytecode Detector Creators
Welcoming Samantha Wessels: Snyk's New Vice President, EMEA Sales
What You Should Know About npm Packages 'colors' and 'faker'
New years resolution: Don't show my security tokens when hacking my demo application on stage
Traditionally, we start the new year with resolutions. We want to do more good things, like working, other things we try to eliminate. Considering the latter, my 2022 resolution is to stop accidentally exposing confidential information while I hack my application during demos on stage or similar. Yes, this new years resolution sounds very specific, and it has an excellent security horror story behind it…
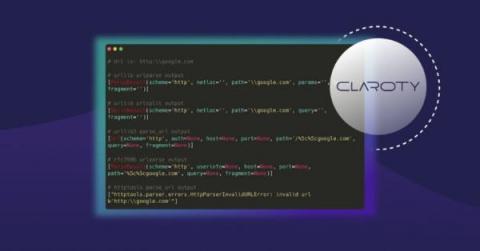
URL confusion vulnerabilities in the wild: Exploring parser inconsistencies
URLs have forever changed the way we interact with computers. Conceptualized in 1992 and defined in 1994, the Uniform Resource Locator (URL) continues to be a critical component of the internet, allowing people to navigate the web via descriptive, human-understandable addresses. But with the need for human readability came the need for breaking them into machine-usable components; this is handled with URL parsers.
Open source maintainer pulls the plug on npm packages colors and faker, now what?
On January 8, 2022, the open source maintainer of the wildly popular npm package colors, published colors@1.4.1 and colors@1.4.44-liberty-2 in which they intentionally introduced an offending commit that adds an infinite loop to the source code. The infinite loop is triggered and executed immediately upon initialization of the package’s source code, and would result in a Denial of Service (DoS) to any Node.js server using it.
FTC highlights the importance of securing Log4j and software supply chain
Earlier this week, the FTC issued a warning to companies regarding the Log4j vulnerability. Given the rampant exploitation of the recently discovered vulnerabilities in this ubiquitous open source logging package, it’s encouraging to see the agency take this rare step, beginning to form a firm stance on software supply chain security. Although this increased scrutiny from the FTC may at first seem daunting, violations can be remediated with the right practices.