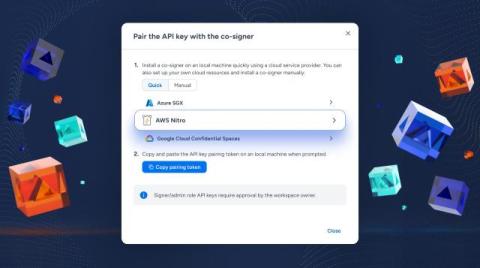
Support for AWS Nitro Enclaves on Fireblocks
At Fireblocks, we know that our customers employ a variety of different cloud configurations for their own internal systems. That’s why we’re excited to announce that Fireblocks now supports Amazon Web Services (AWS) Nitro Enclaves. With this new development, Fireblocks customers building products on AWS can now utilize Nitro Enclaves to run their Fireblocks API Co-Signer.