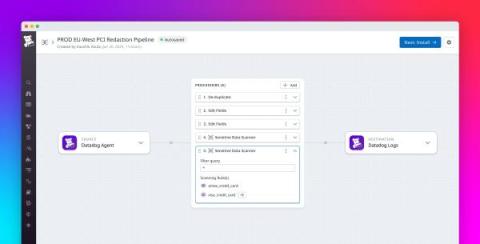
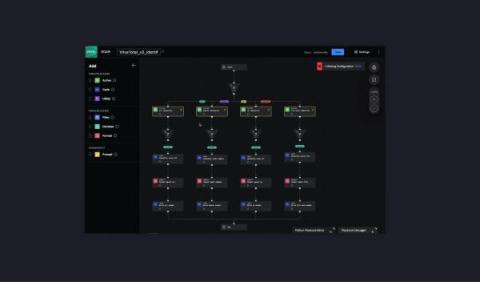
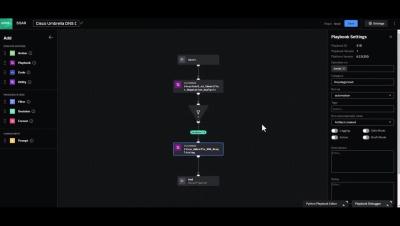
Explore the AI Frontier in Splunk's State of Security 2024
Change in the cybersecurity industry is inevitable, and 2024 brings upheaval in the form of geopolitical tensions, rigorous compliance requirements, and of course, the rapid acceleration of generative AI.