It's About the Economics of Machine Data, Stupid
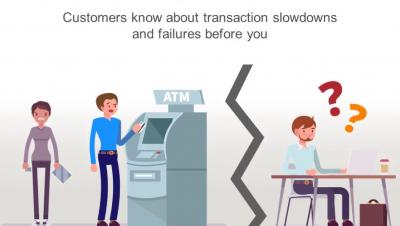
If I never hear the phrase “Data is the new oil” again I will die a happy man. Don’t get me wrong – I wholeheartedly believe in the value of data and its power to transform businesses – but the frequency with which I hear this phrase reminds me we are still in the adolescent fascination phase of how we look at the power of data.