Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
API
What is API Authentication?
Security with a High Engineer-to-AppSec Ratio: Insights from Jeevan Singh
Navigating the delicate balance between an expanding number of engineers and the imperative for robust Application Security (AppSec) practices is no small feat. In this interview, we delve into the invaluable perspective of Jeevan Singh, the Director of Security Engineering at Rippling, the #1 workforce management platform. He shares insights and strategies that have allowed him in his career to successfully navigate the intricate maze of security amidst a high engineer-to-AppSec ratio.
Leveraging OpenAPI as a Core Element of API and Application Security
How Unsecured APIs Can Eat Up Retail Revenue
Introducing Bearer Assistant
Artificial Intelligence (AI) is a hot topic these days, especially across the security industry. There's hardly a day when we don't read about its potential to create an impact on our lives, for better or worse. As a security company, we truly believe in the potential of AI, but we didn't want to jump into the deep end without careful consideration as we followed the buzz with a healthy amount of skepticism.
The Ultimate 2024 API Security Checklist
Bolstering API Security: Introducing Wallarm's API Attack Surface Management (AASM)
In the fast-paced digital world, think of Application Programming Interfaces (APIs) as the threads that stitch together the fabric of our tech ecosystems. They're often overlooked, quietly ensuring that your apps communicate seamlessly and keep the digital world running smoothly. The majority of organizations grapple with a common challenge — limited visibility into their public API attack surfaces.
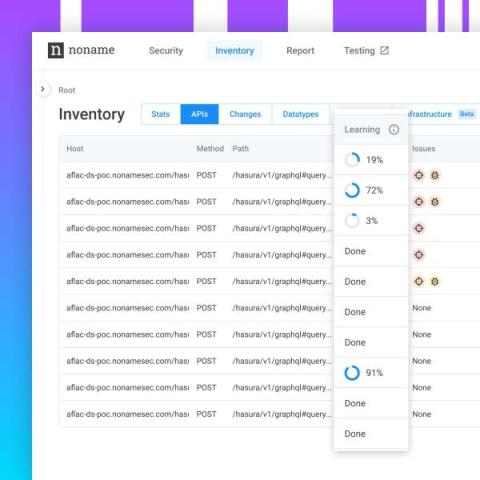
Noname Security Platform Updates: November 2023
We are excited to provide the latest news and features about the Noname Security platform. These features help you protect your APIs from a broader range of attacks, improve your security posture, and simplify your API security operations. In this blog post, we’ll dive into the latest updates that will redefine how you interact with our product across the four pillars — Runtime Security, Discovery, Posture Management, and Active Testing.