Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
MITRE ATT&CK
CrowdStrike Participates in Center for Threat-Informed Defense OceanLotus Project, the First Public Adversary Emulation Plan Combining macOS and Linux
The MITRE ATT&CK framework, a key resource for helping organizations defend against cyberattacks, is critical to advancing cybersecurity research. The MITRE Engenuity Center for Threat-Informed Defense’s public library of adversary-specific emulation plans has become a valuable component of the ATT&CK framework. Each plan in the library provides comprehensive ATT&CK tactics and techniques employed by well-known adversaries.
Devo Exchange - MITRE ATT&CK content packs & alerts
Coffee Talk with SURGe: The Interview Series featuring Cat Self
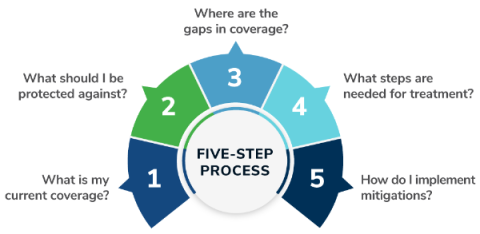
Free Template: MITRE ATT&CK Detection Maturity Assessment & Guide
The threat landscape has evolved rapidly in recent years due to major changes in the way organizations operate and adopt new technologies. Cloud services such as Software-as-a-Service (SaaS) and Infrastructure-as-a-Service (IaaS) have seen massive growth over the last decade. With accelerated digital transformation, increased remote working and cloud adoption, the attack surface has increased for most organizations.
A Simplified Overview of the MITRE ATT&CK Framework
In the world of cybersecurity, have you ever wondered about the inner workings of threat actors as they attempt to breach systems, their methods, tactics, and strategies, and how they seamlessly converge to execute a successful attack? It's not merely about initiating an attack but also the strategies they utilize to remain concealed within the system, allowing them to persistently operate and ultimately achieve their goals.
How to Defeat MITRE ATT&CK Reconnaissance Techniques
MITRE ATT&CK Reconnaissance (TA0043) techniques section maps out how threat actors gather information about potential targets. Like other ATT&CK tactics (like initial access and lateral movement), reconnaissance provides useful threat intelligence on adversary tactics, techniques, and procedures (TTPs). It is a realistic approximation of what will happen if you become a target.