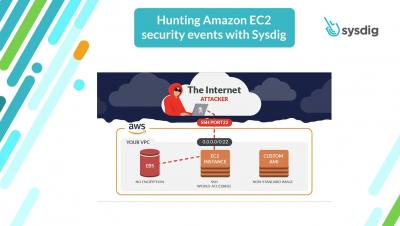
Sysdig CSPM remediates security issues in seconds
Automate security issue fixes in seconds and reduce cloud risk with Sysdig. Let's dig in! We know cloud teams have tons of security issues. You can be spending hours trying to understand if those findings pose a real risk in your cloud environment. So, how can you shorten the time needed to triage every misconfiguration and take action on those that really matter to you? Discover how Sysdig aggregates security findings by root cause and prioritizes remediation based on impact and risk.