Cloud Security Meets GenAI: Introducing Sysdig Sage
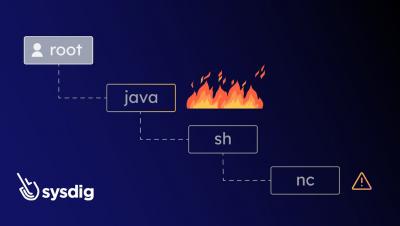
The scale and complexity of the cloud has redefined the security battleground. Threats can now be anywhere and attacks are far, far faster. We are proud to introduce Sysdig Sage - an AI-powered security assistant that redefines what it means to respond at cloud speed. With Sage's help, you can take action on an attack in under 60 seconds! Using multi-domain correlation, multi-step reasoning, and - most importantly - runtime insights, Sage speeds up your investigation by prioritizing security events, providing context, and helping you assess risk.