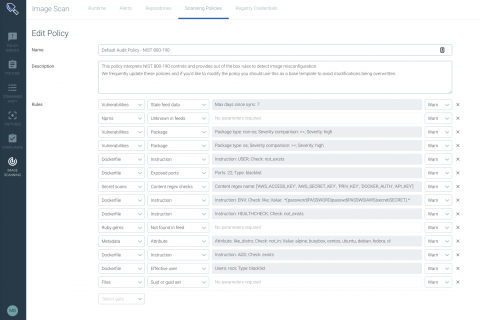
Shifting Left Is a Lie... Sort of
It would be hard to be involved in technology in any way and not see the dramatic upward trend in DevOps adoption. In their January 2019 publication “Five Key Trends To Benchmark DevOps Progress,” Forrester research found that 56 percent of firms were ‘implementing, implemented or expanding’ DevOps. Further, 51 percent of adopters have embraced DevOps for either all new or all applications. Clearly, DevOps adoption is here and growing.