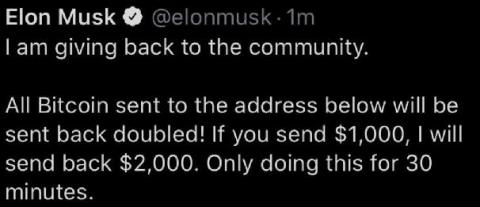
Using the Cost of a Data Breach to Maximize Your ROI on Your Security Tools
The 2020 Cost of Data Breach report from IBM and the Ponemon is out. It provides a detailed analysis of causes, costs and controls that appeared in their sampling of data breaches. The report is full of data, and the website allows you to interact with its information so that you can do your own analysis and/or dig into aspects relevant to you and your industry.