It Takes a Village: The Power of Partnership in Creating Secure Software
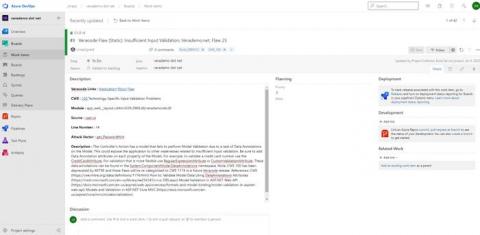
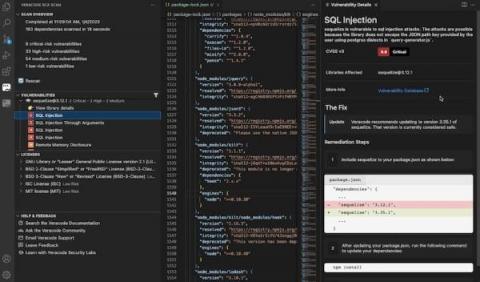
Application security is about so much more than scanning. The Velocity Partner Program aligns Veracode and our Partners as together we deliver application security solutions and services that enable customers to build a secure DevOps program. The Velocity Partner Program empowers our partners in their trusted advisor role to address key security requirements and business challenges customers are facing throughout their application security journey.