Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Hacking
How to Make Your Hackathon Project Stand Out?
The 443 Episode 230 - Successfully Prosecuting a Russian Hacker
Cybercriminal convicted of $90 million SEC earning reports hack
The owner of a Russian penetration-testing company has been found guilty of being part of an elaborate scheme that netted $90 million after stealing SEC earning reports. For nearly three years, 42-year-old Vladislav Klyushin - the owner of Moscow-based cybersecurity firm M-13 - and his co-conspirators had hacked into two US-based filing agents used by publicly-traded American companies to file earning reports to the Securities and Exchange Commission.
Negotiating With Hackers to Unlock Your Data - What You Need to Know!
Why Hackers Love Credentials: Parsing Verizon's 2022 Breach Report
This Valentine's Day, Swipe Left on Hackers
Online dating is one of the fastest-growing industries in the tech world. Online dating has quickly become a sustainable way to remain social and have a relationship with someone other than your cat. But what are the chances that you’ll be swiping right on a hacker? Mobile analytics platform, Adjust, reports that in 2021, 300 million adults used dating apps worldwide with 20 million users paying for premium features.
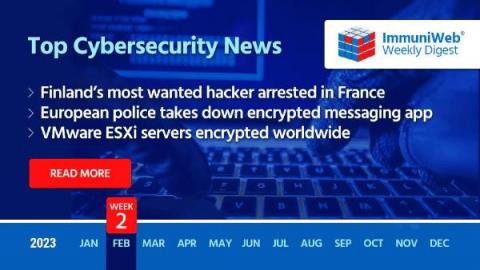
French police arrested Julius "Zeekill" Kivimäki, one of the most notorious hackers, wanted by Finland's authorities
Read also: A global phishing syndicate used over 500 apps to steal data from phones, MITRE unveils a free tool to help organizations strengthen cyber resilience, and more.