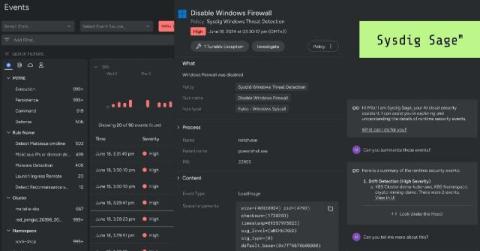
What Are the 6 Most Common Forms of Phishing?
In this video, learn the six most common forms of phishing, how to identify them, and how to protect your organization from them. Learn more about JumpCloud SSO and phishing-resistant passwordless authentication with JumpCloud Go: Resources and social media.