Why DevSecOps is Going Passwordless
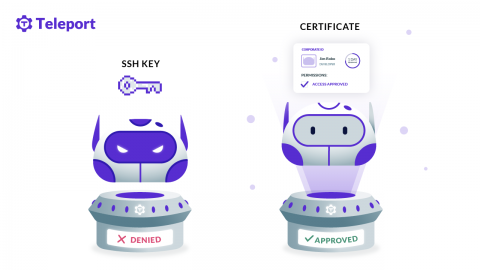
I talk to a lot of engineers every day. SREs. Systems Architects. Security Engineers. What I am hearing from them is that they are moving away from passwords — both in their personal lives, opting for more secure forms of authentication like biometrics and second factors, and at work. It just doesn’t make sense anymore to protect your personal bank with a second factor, but to share around an SSH key to access critical server infrastructure.