How to Improve Cybersecurity with Datadog's End-to-End Observability Tailored For the US Government
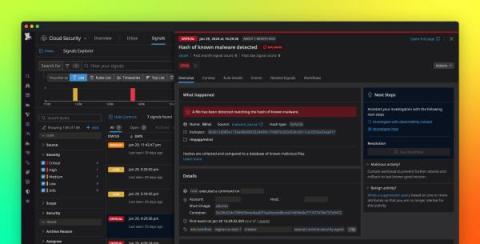
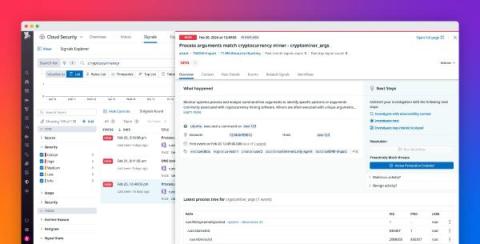
Watch this webinar to learn how: The Datadog platform helps agencies work across silos that separate development, operations, and security teams to foster collaboration and improve cybersecurity posture Datadog has committed to higher levels of security authorizations, including FedRAMP® High, and Impact Level 5 for DoD agencies Our end-to-end observability platform helps agencies address the unique challenges faced by IT leaders in government, including compliance with stringent security standards outlined in Executive Orders and other regulatory directives.