Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Zero Trust
Five worthy reads: Cybersecurity mesh-An extension of the Zero Trust Network
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week let’s zoom in on cybersecurity mesh, which brings a twist to the existing security architecture with a distributed approach.
Why retailers must adopt a Zero Trust approach during this holiday season
The pandemic accelerated a trend that was already gaining increased traction: the preference for shopping online. The last eighteen months have brought a surge to the eCommerce industry, with consumers of all ages learning how to order items online. Competition has never been fiercer for online retailers, which means it’s not just quality products and customer service that companies must focus on.
The Zero-Trust Journey in 5 Phases
For a concept that represents absence, zero trust is absolutely everywhere. Companies that have explored how to embark upon zero-trust projects encounter daunting challenges and lose sight of the outcomes a zero-trust approach intends to achieve. Effective zero-trust projects aim to replace implicit trust with explicit, continuously adaptive trust across users, devices, networks, applications, and data to increase confidence across the business.
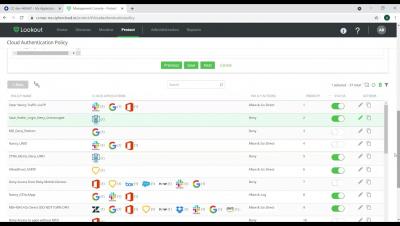
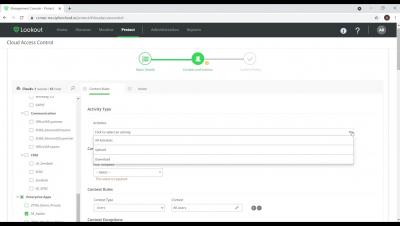
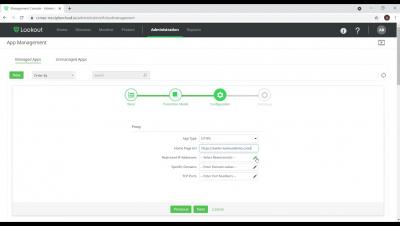
Lookout ZTNA - Setting up an access policy for unmanaged devices
Zero Trust? Don't Forget Your Mobile Fleet
Zero doubt about the direction of zero trust security
The adoption of zero trust is about to change dramatically. In May, the Biden administration announced its cybersecurity Executive Order (EO), stressing the urgency of modernized access and cybersecurity defenses. Consequently, many enterprises can no longer ignore the necessity of investing in zero trust architectures.