Mitigating Risks in Software Supply Chain
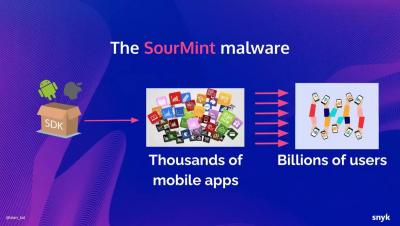
By 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains (Gartner) which are only becoming increasingly complex due to the changes in how modern software is built. These trends, together with new federal regulations, require organizations to take action to ensure the security and integrity of their software. But this is easier said than done.