Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Choosing an Industrial Cybersecurity Framework
Protecting Industrial Operations With Shop-Floor to Top-Floor Visibility
Infosec Problems For 2019 and Beyond: Patching, Bug Bounties and Hype
Details of a Virtual Box 0-day privilege escalation bug were disclosed on GitHub earlier this week. This was the work of independent Russian security researcher Sergey Zelenyuk, who revealed the vulnerability without any vendor coordination as a form of protest against the current state of security research and bug bounty programs.
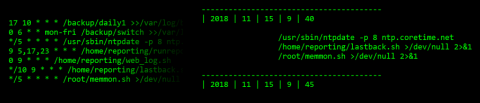
Cronview
Throughout my years working with Unix flavoured environments, one of the headaches I’ve had to deal with is cron. Don’t get me wrong, I love cron, it’s a necessity for any operation of such servers, however, there usually comes a point when the size of list reaches a critical mass that makes visualising the execution times a challenge.
A Non-Partisan Threat: Cybersecurity and its Impact on Democracy
Egnyte Connect for Desktop 3.0: Design Meets Functionality
The first thing most of us notice after a major software update is a completely redesigned user interface. However, a new user experience is typically the result of a shift in product focus. In version 2.0, our primary focus was on intelligent data retrieval. The idea was to allow users to work on any file in the same way they would for files stored on their machine(s).
Tripwire Data Collector Increases Operational Technology Visibility With Enhanced Web Scripting Capability
Tripwire Data Collector has been providing industrial organizations with visibility into their operational technology (OT) environments since its release in mid-2018.
The Many Ways your Phone Communicates
Are you familiar with all the ways that your smart phone communicates? The other evening, at dinner, I was describing to a friend how the VPN software I use on my phone masks my location when I am on the internet. Sometimes, I am in Helsinki, and other times, I may be in another part of the world.
Turning Malware Trends into Proactive Behaviors
Most of the industry agrees: malware is on the rise. My news feed rarely manages a week without an incident making the headlines. Here are some of the most recent events I’ve seen...