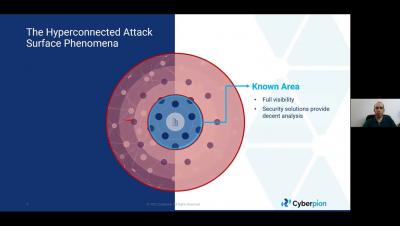
How Your Employees Are Expanding the Attack Surface
The security of the enterprise has been dramatically disrupted due to hybrid and work-from-home (WFH) environments. Security teams are struggling to grasp the scope of their organizations’ devices, tools, and apps as employees download, log in, and use their preferred software and shortcuts from their home offices.