Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
IONIX
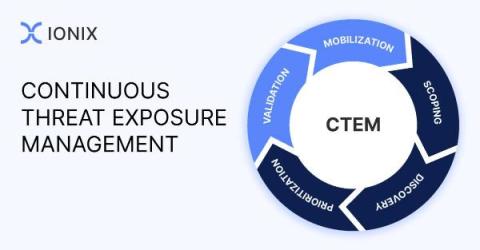
Gartner CTEM Starts with EASM
External Attack Surface Management(EASM) has emerged as a cybersecurity gold standard – a core component of modern cybersecurity programs. As digital organizations have grown more complex, getting the whole picture of the external attack surface – what’s connected to what and how this could pose danger – is a maze that only-world-class EASM solutions have been able to successfully navigate.
The State of Citrix Zero-Day Vulnerabilities 2023
Critical zero-day Citrix CVE-2023-3519 is still being exploited two months after Citrix released a patch. IONIX research found that 19% of the CVE-2023-3519 vulnerabilities are still unmitigated in comparison to only 3% among IONIX customers. In addition, IONIX customers were able to resolve this critical risk three times faster.
Cisco VPN Zero-Day exploited by ransomware gangs (CVE-2023-20269) - Insights and best practices for defense Copy
In the tech security scene, we’re always on the lookout for new vulnerabilities, especially when they are already exploited in the wild. The latest zero-day CVE-2023-20269 is hitting Cisco’s Adaptive Security Appliance VPN features. The attack surface scan conducted by IONIX research on a sample of organizations indicates that 13% of these appliances are potentially vulnerable through at least one interface.
Cisco VPN Zero-Day exploited by ransomware gangs (CVE-2023-20269) - Insights and best practices for defense
In the tech security scene, we’re always on the lookout for new vulnerabilities, especially when they are already exploited in the wild. The latest zero-day CVE-2023-20269 is hitting Cisco’s Adaptive Security Appliance VPN features. The attack surface scan conducted by IONIX research on a sample of organizations indicates that 13% of these appliances are potentially vulnerable through at least one interface.
Vulnerability Assessment Methodology: How to Perform a Vulnerability Assessment
There are flaws in every organization’s IT infrastructure, along with software that requires patching. These flaws could arise from various sources, such as human errors during software coding. Hackers are always on the lookout to exploit these flaws and applications. However, by following a vulnerability assessment methodology to perform vulnerability assessments, organizations can identify these weaknesses before the cyber adversaries do.
32 Cybersecurity and IT Management Professionals Share Their Favorite CISO Interview Questions
The role of the CISO (Chief Information Security Officer) is one of the most important in any organization, and finding the right professional for the job is vital. The CISO leads the company’s information security strategy and bears the ultimate responsibility for the company’s security posture and how effectively it protects its information systems.
27 Cybersecurity Professionals and Business & Technology Leaders Reveal the Most Important Cyber Risk Trends Companies Need To Look Out for
Cyber risk trends are constantly evolving, driven by the pace of technological advancements that streamline business processes yet can introduce vulnerabilities in your company’s attack surface. With increased use of SaaS, cloud solutions, APIs, and third-party services, companies have many exposed and connected internet-facing assets that they’re unaware of, providing an open door for attackers to exploit.
IONIX Wins Two 2023 Silver Globee Awards
IONIX has won two prestigious 2023 Globee® Awards, which include a Silver in the 3rd Annual Globee® Information Technology (IT) Awards for Best Attack Surface Management Product and a Silver in the 3rd Annual Globee® Disruptor Award for Cyber Security Software. These awards come on the heels of a Gold 2023 Globee® Cybersecurity Award for Best Security Software.
Be Smart About Attack Surface Management Automation
Smart automation in ASM refers to the application of intelligent and adaptive technologies and tools to automate the attack surface management process. By leveraging machine learning algorithms and artificial intelligence technologies, enterprises can automate discovery and threat exposure, drastically reducing the time and resources required for the process. They can also minimize false positives and false negatives.