Get Management Buy-in with AppSec Metrics
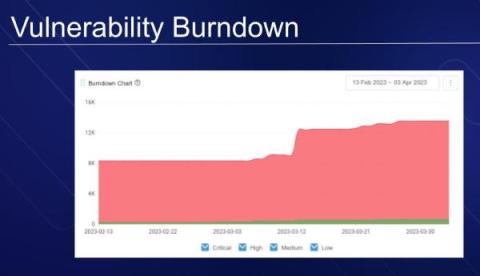
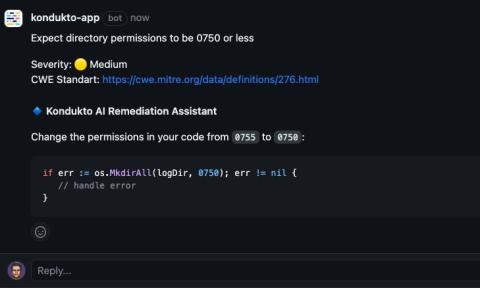
Getting management to back your application security plans can be a tough sell. Metrics are vital because they help you understand how effective your initial cybersecurity measures are and how to turn them into measurable data that's easy for everyone to understand. This article will explore how to use metrics to get the support you need and make your application security programs more effective.