The Power of Platform-Native Consolidation in Application Security
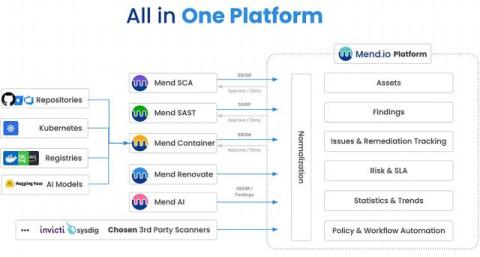
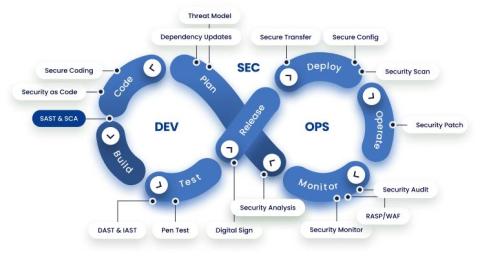
The application security landscape is shifting as organizations move away from a fragmented ecosystem of point solutions towards a unified platform such as the Mend AppSec Platform. Leveraging these platform-specific strengths brings numerous advantages: streamlined workflows, a cross-product workflow engine, a consolidated data model that enhances security posture, and developers that can focus fully on innovation.