How the public sector benefits from Splunk's market-leading SIEM platform
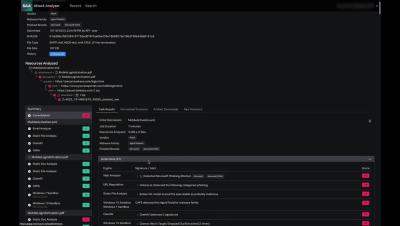
A traditional endpoint security solution (EDR/XDR) isn't cutting it anymore today. Learn more about how our market-leading SIEM solution can help organisations detect what endpoint solutions miss and other critical benefits to tackle the challenges of today's threat landscape.